Configure AWS Roles for AWS Clean Rooms
The following role configurations are required on the AWS clean Room owner's AWS account to enable LiveRamp Clean Room to orchestrate AWS Clean Rooms. Use the following LiveRamp Clean Room production IAM clean room role when required:
arn:aws:iam::169573774239:role/service/habu_clean_room_role
Prerequisites
All the partners collaborating in a given AWS clean room should host their data on S3 in the same AWS region.
S3 data should be cataloged in AWS Glue Catalog.
Overall Steps
Perform the following overall steps to configure a AWS Roles for AWS Clean Rooms:
For information on performing these steps, see the sections below.
Create IAM Roles in Your AWS Account
All partners should create the following two IAM roles in their AWS account which hosts the S3 data:
CleanRoomServiceRole
CleanRoomResourceRole
This role will have a trust relationship with the native AWS Clean Rooms service.
Note
The policy document will have permission to access raw data on S3 and Glue catalog. Only AWS Clean Rooms service will have access to this and LiveRamp Clean Room will not have access to raw data.
Create the following "CleanRoomServicePolicy" policy and attach it to the service role above. Set the maximum session duration to 8 hours. Make sure to substitute proper values for the following macros:
AWS_REGION
AWS_ACCOUNT_ID
AWS_S3_BUCKET
{ "Version": "2012-10-17", "Statement": [ { "Sid": "NecessaryGluePermissions", "Effect": "Allow", "Action": [ "glue:GetDatabase", "glue:GetDatabases", "glue:GetTable", "glue:GetTables", "glue:GetPartition", "glue:GetPartitions", "glue:BatchGetPartition" ], "Resource": [ "arn:aws:glue:AWS_REGION:AWS_ACCOUNT_ID:database/*", "arn:aws:glue:AWS_REGION:AWS_ACCOUNT_ID:table/*", "arn:aws:glue:AWS_REGION:AWS_ACCOUNT_ID:table/*/*", "arn:aws:glue:AWS_REGION:AWS_ACCOUNT_ID:catalog" ] }, { "Effect": "Allow", "Action": [ "glue:GetSchema", "glue:GetSchemaVersion" ], "Resource": [ "*" ] }, { "Sid": "NecessaryS3BucketPermissions", "Effect": "Allow", "Action": [ "s3:GetBucketLocation", "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::AWS_S3_BUCKET" ], "Condition": { "StringEquals": { "s3:ResourceAccount": [ "AWS_ACCOUNT_ID" ] } } }, { "Sid": "NecessaryS3ObjectPermissions", "Effect": "Allow", "Action": [ "s3:GetObject", "s3:PutObject", "s3:GetBucketLocation", "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::AWS_RESULTS_DATA_S3_BUCKET", "arn:aws:s3:::AWS_RESULTS_DATA_S3_BUCKET/*" ], "Condition": { "StringEquals": { "s3:ResourceAccount": [ "AWS_ACCOUNT_ID" ] } } } ] }The trust relationship on the "CleanRoomServiceRole" should look like the following:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "RoleTrustPolicyForCleanRoomsService", "Effect": "Allow", "Principal": { "Service": "cleanrooms.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }
This role will have a trust relationship with the LiveRamp Clean Room IAM clean room role:
arn:aws:iam::169573774239:role/service/habu_clean_room_role
The LiveRamp Clean Room role will assume permissions into the client’s resource role and perform clean room resource management operations, for example, create or delete collaboration, membership, configured tables, configured table associations, and configured table analysis rules; execute protected queries, and so on. Set the maximum session duration to 8 hours. Create the following two policies and attach to the above resource role.
Create the following "CleanRoomManagementPolicy" policy and attach it to the above resource role. Make sure to substitute the ARN of the "CleanRoomServiceRole" you created for the "CLEAN_ROOM_SERVICE_ROLE_ARN" macro in this example:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "CleanRoomsCreateAccess", "Effect": "Allow", "Action": [ "cleanrooms:CreateCollaboration", "cleanrooms:DeleteCollaboration", "cleanrooms:DeleteMember", "cleanrooms:GetCollaboration", "cleanrooms:ListCollaborations", "cleanrooms:ListMembers", "cleanrooms:UpdateCollaboration", "cleanrooms:ListTagsForResource", "cleanrooms:UntagResource", "cleanrooms:TagResource" ], "Resource": "*" }, { "Sid": "CleanRoomsAccess", "Effect": "Allow", "Action": [ "cleanrooms:BatchGetSchema", "cleanrooms:CreateConfiguredTable", "cleanrooms:CreateConfiguredTableAnalysisRule", "cleanrooms:CreateConfiguredTableAssociation", "cleanrooms:CreateMembership", "cleanrooms:CreateAnalysisTemplate", "cleanrooms:DeleteAnalysisTemplate", "cleanrooms:DeleteConfiguredTable", "cleanrooms:DeleteConfiguredTableAnalysisRule", "cleanrooms:DeleteConfiguredTableAssociation", "cleanrooms:DeleteMembership", "cleanrooms:GetCollaboration", "cleanrooms:GetConfiguredTable", "cleanrooms:GetConfiguredTableAnalysisRule", "cleanrooms:GetConfiguredTableAssociation", "cleanrooms:GetMembership", "cleanrooms:GetSchema", "cleanrooms:GetSchemaAnalysisRule", "cleanrooms:ListCollaborations", "cleanrooms:ListConfiguredTableAssociations", "cleanrooms:ListConfiguredTables", "cleanrooms:ListMembers", "cleanrooms:ListMemberships", "cleanrooms:ListSchemas", "cleanrooms:UpdateConfiguredTable", "cleanrooms:UpdateConfiguredTableAnalysisRule", "cleanrooms:UpdateConfiguredTableAssociation", "cleanrooms:UpdateMembership", "cleanrooms:ListTagsForResource", "cleanrooms:UntagResource", "cleanrooms:TagResource" ], "Resource": "*" }, { "Sid": "PassServiceRole", "Effect": "Allow", "Action": [ "iam:PassRole" ], "Resource": "CLEAN_ROOM_SERVICE_ROLE_ARN", "Condition": { "StringEquals": { "iam:PassedToService": "cleanrooms.amazonaws.com" } } }, { "Sid": "ListRolesToPickServiceRole", "Effect": "Allow", "Action": [ "iam:ListRoles" ], "Resource": "*" }, { "Sid": "GetRoleAndListRolePoliciesToInspectServiceRole", "Effect": "Allow", "Action": [ "iam:GetRole", "iam:ListRolePolicies" ], "Resource": "CLEAN_ROOM_SERVICE_ROLE_ARN" }, { "Sid": "ConsoleDisplayTables", "Effect": "Allow", "Action": [ "glue:GetDatabase", "glue:GetDatabases", "glue:GetTable", "glue:GetTables", "glue:GetPartition", "glue:GetPartitions", "glue:GetSchema", "glue:GetSchemaVersion", "glue:BatchGetPartition" ], "Resource": "*" }, { "Sid": "EstablishLogDeliveries", "Effect": "Allow", "Action": [ "logs:CreateLogDelivery", "logs:GetLogDelivery", "logs:UpdateLogDelivery", "logs:DeleteLogDelivery", "logs:ListLogDeliveries" ], "Resource": "*", "Condition": { "ForAnyValue:StringEquals": { "aws:CalledVia": "cleanrooms.amazonaws.com" } } }, { "Sid": "SetupLogGroupsDescribe", "Effect": "Allow", "Action": [ "logs:DescribeLogGroups" ], "Resource": "*", "Condition": { "ForAnyValue:StringEquals": { "aws:CalledVia": "cleanrooms.amazonaws.com" } } }, { "Sid": "SetupLogGroupsCreate", "Effect": "Allow", "Action": [ "logs:CreateLogGroup" ], "Resource": "arn:aws:logs:*:*:log-group:/aws/cleanrooms*", "Condition": { "ForAnyValue:StringEquals": { "aws:CalledVia": "cleanrooms.amazonaws.com" } } }, { "Sid": "SetupLogGroupsResourcePolicy", "Effect": "Allow", "Action": [ "logs:DescribeResourcePolicies", "logs:PutResourcePolicy" ], "Resource": "*", "Condition": { "ForAnyValue:StringEquals": { "aws:CalledVia": "cleanrooms.amazonaws.com" } } }, { "Sid": "ConsoleLogSummaryQueryLogs", "Effect": "Allow", "Action": [ "logs:StartQuery" ], "Resource": "arn:aws:logs:*:*:log-group:/aws/cleanrooms*" }, { "Sid": "ConsoleLogSummaryObtainLogs", "Effect": "Allow", "Action": [ "logs:GetQueryResults" ], "Resource": "*" } ] }Create the following "CleanRoomQueryExecutionPolicy" policy and attach it to the above resource role:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "CleanRoomsAccess", "Effect": "Allow", "Action": [ "cleanrooms:GetProtectedQuery", "cleanrooms:ListProtectedQueries", "cleanrooms:StartProtectedQuery", "cleanrooms:UpdateProtectedQuery" ], "Resource": "*" } ] }The trust relationship on the "CleanRoomResourceRole" should look like the following:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": [ "arn:aws:iam::169573774239:role/service/habu_clean_room_role" ] }, "Action": "sts:AssumeRole" } ] }
Add Client-Side S3 Bucket Permissions
Note
This step is only applicable to the owner of the clean room if they want the query results to be written directly to their S3 bucket instead of the bucket hosted by LiveRamp Clean Room. Partners can ignore this step.
To configure client-side S3 permissions:
Note
Keep the following in mind when configuring client-side S3 bucket permissions:
The results S3 bucket should be in the same region as the source data S3 bucket and AWS Collaboration.
Ensure that the LiveRamp Clean Room role has read access to the S3 bucket, for example:
If "CLEAN_ROOM_SERVICE_ROLE_ARN" is the ARN of the service role you created earlier and "AWS_RESULTS_DATA_S3_BUCKET" is the bucket where the results data are stored, then the LiveRamp Clean Room role ARN should have read access to this bucket. This is so the results can be fetched, shown in the UI, and sent to activation channels if required.
Navigate to the S3 source page in AWS console.
Select the S3 bucket that has the results data.
Under the Permissions tab, add the following bucket policy to permit LiveRamp Clean Room to read the results (modify accordingly).
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CleanRoomServiceResultsPut",
"Effect": "Allow",
"Principal": {
"AWS": "CLEAN_ROOM_SERVICE_ROLE_ARN"
},
"Action": "s3:PutObject",
"Resource": [
"arn:aws:s3:::AWS_RESULTS_DATA_S3_BUCKET",
"arn:aws:s3:::AWS_RESULTS_DATA_S3_BUCKET/*"
]
},
{
"Sid": "HabuServiceResultsGet",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::169573774239:role/service/habu_clean_room_role"
},
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::AWS_RESULTS_DATA_S3_BUCKET",
"arn:aws:s3:::AWS_RESULTS_DATA_S3_BUCKET/*"
]
}
]
}Add Client-Side S3 Bucket to an AWS Credential
From the navigation menu, select Clean Room → Credentials to open the Credentials page.
Click .
Enter a descriptive name for the credential.
For the Credentials Type, select "AWS Clean Room Credentials".
Enter the following parameters associated with your AWS configuration:
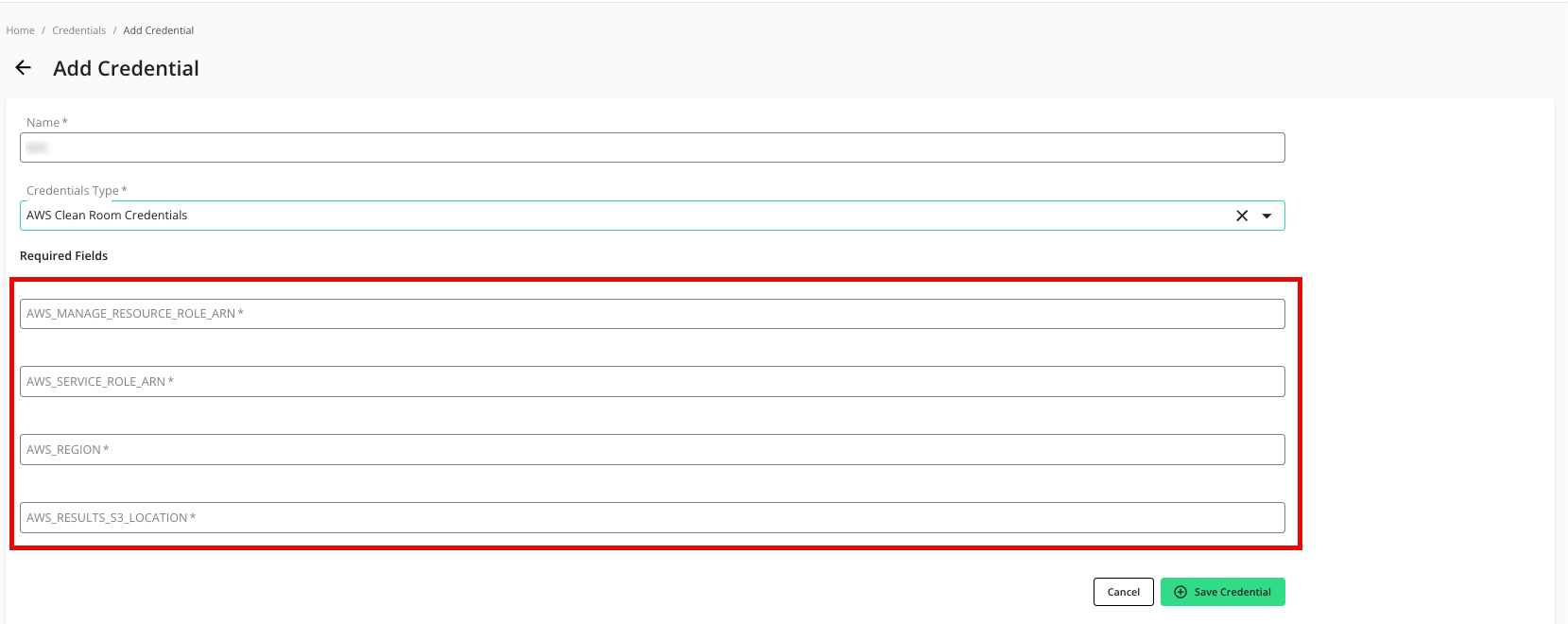
AWS_MANAGE_RESOURCE_ROLE_ARN: Enter the IAM role ARN of "CleanRoomResourceRole" created in the "Create IAM Roles in Your AWS Account" section above.
AWS_SERVICE_ROLE_ARN: Enter the IAM role ARN of "CleanRoomServiceRole" created in the "Create IAM Roles in Your AWS Account" section above.
AWS_REGION: Enter your AWS region.
AWS_RESULTS_S3_LOCATION: Enter either "s3://AWS_RESULTS_DATA_S3_BUCKET/path_to_folder" or "s3://AWS_RESULTS_DATA_S3_BUCKET".
Click .