Configuring BigQuery Permissions for BigQuery Clean Rooms
Instructions on how to configure BigQuery permissions for use within Clean Room, including steps for setting up roles, assigning permissions, and verifying the configuration
Prior to orchestrating BigQuery Clean Rooms in LiveRamp Clean Room, it is important to configure the necessary permissions in the Google Cloud Platform (GCP) and LiveRamp Clean Room, as well as enable certain APIs for your project. The following procedures apply to clean room owners and partners orchestrating BigQuery clean rooms and enable LiveRamp Clean Room to effectively manage data, billing, and partner collaborations.
Overall Steps
Perform the following overall steps to configure BigQuery permissions for BigQuery Clean Rooms:
For information on performing these steps, see the sections below.
Prerequisites
Before configuring BigQuery permissions for BigQuery Clean Rooms, note the following:
LiveRamp Clean Room recommends configuring your BigQuery instance in the US-multi-region for U.S. customers and the EU-multi-region for EU customers. This configuration enhances flexibility, especially when collaborating with partners across different regions.
There are three service accounts involved in the process of configuring the required GCP and BigQuery permissions to orchestrate BigQuery Clean Rooms in LiveRamp Clean Room:
Owner service account
Partner service account (follow the same steps as the owner service account)
LiveRamp Clean Room service account
The steps for the owner service account and partner service account are the same. If you are a clean room partner, follow the same steps below where the owner service account is referenced.
Create a GCP Project
Create a GCP Project associated with the owner service account including the "Service Account" and "Service Account Key".
Note the "Project ID" and "Credential JSON". You'll need these for the "Configure BigQuery Credentials in LiveRamp Clean Room" section below.
Ensure that the created project is associated with a billing account.
Create Authorized Views
For LiveRamp Clean Room to read data from Google BigQuery, authorized views must be created, which can only be done by users who have access to the data itself.
Note
LiveRamp recommends permitting LiveRamp to create the authorized views rather than letting the customer create them in order to mitigate manual maintenance requirements by the customer when changes are made to the data over time. If a customer creates authorized views and makes any changes to the underlying data (for example, columns added or removed), this will result in Clean Room run failures, which must be mediated by the customer. LiveRamp is unable to support troubleshooting and resolution in this case. If LiveRamp creates the views, all maintenance is managed by LiveRamp.
If you do want to create authorized views rather than letting LiveRamp create them, reach out to LiveRamp Community portal for more information.
Configure Permissions
Note
Keep in mind the following when configuring permissions:
The LiveRamp Clean Room service account has access to the source data.
LiveRamp manages the authorized views. If there are changes to the source data, they are managed by LiveRamp.
LiveRamp Clean Room features, such as row-level filtering and adding custom logic when configuring datasets in a clean room, will be available to the clean room owner.
LiveRamp simplifies authorized views and removes related ambiguity and complexity.
To configure permissions, do the following:
Create custom roles where indicated below and configure the following permissions for the owner and LiveRamp Clean Room service accounts:
Service Account | Roles/Permissions | Permission Level | Purpose |
|---|---|---|---|
Owner | BigQueryMetaDataViewer | Table | Enables data connections to reach metadata. |
Owner | Create a custom role named "LiveRamp Clean Room Authorized View Role" with the following permissions:
| Project | Used to create a shared dataset and create authorized views in the shared dataset. |
Owner | Analytics Hub Admin | Project | Enables LiveRamp Clean Room to create Exchange and Listing. |
NoteThe following Custom Roles should also be created and permissions configured. However, they cannot be applied to the LiveRamp Clean Room service account until the service account has been generated (see the "Generate a Service Account and Understand Billing Considerations" section below). When the service account has been generated, you can apply the following roles to it. | |||
LiveRamp Clean Room | Create a Custom Role named "LiveRamp Clean Room BigQuery Job" with the following permissions:
Recommended for feature completeness:
| Project | Used to orchestrate the job. If not provided, LiveRamp Clean Room will pass through the compute costs |
LiveRamp Clean Room | If you have an Organization IAM policy restriction (IP or domain), create a Custom Role named "LiveRamp Clean Room Analytics Hub Subscriber" with the following permissions:
| Project | Used to subscribe to the listings ephemerally |
Enable Project-Level API
Note
This applies to both the owner and partner at the project level, as APIs cannot be enabled at the dataset level. This is a Google-defined process for working in GCP BigQuery Clean Rooms.
Enable the "Analytics Hub API" at the project level. For more information on managing your APIs, see "Enabled APIs & Services".
Now that you've configured the required permissions in BigQuery, you're ready to configure your BigQuery credentials.
Configure BigQuery Credentials in LiveRamp Clean Room
To configure BigQuery credentials in LiveRamp Clean Room, do the following:
From the LiveRamp Clean Room navigation pane, select Data Management → Credentials.
Click
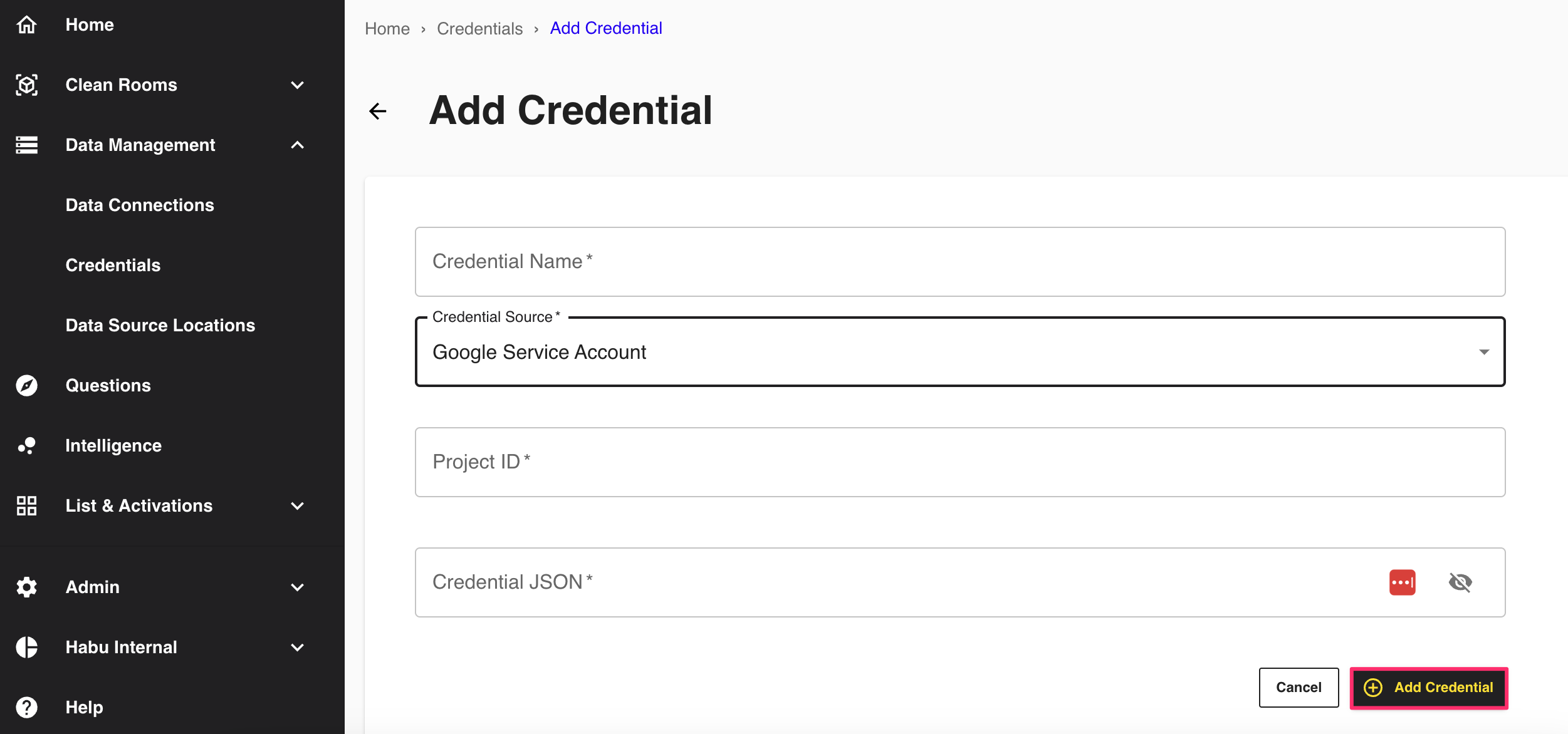
Complete the following fields:
Name: Enter the credential name.
Credentials Type: Select Google Service Account from the list.
Project ID: Enter the project ID (see the "Create a GCP Project" section above)
Credential JSON: Enter the credential JSON (see the "Create a GCP Project" section above)
Click .
Generate a Service Account and Understand Billing Considerations
The LiveRamp Clean Room service account is used to run queries on the selected GCP billing project. This is done at the clean room level.
Each time a new shared clean room is created, a new service account is automatically created. The service account must be added to the GCP billing project and the proper roles applied from the "Create Authorized Views" section above.
From the LiveRamp Clean Room navigation pane, select Clean Rooms → Clean Rooms.
Click
Select Google Cloud BigQuery and click .

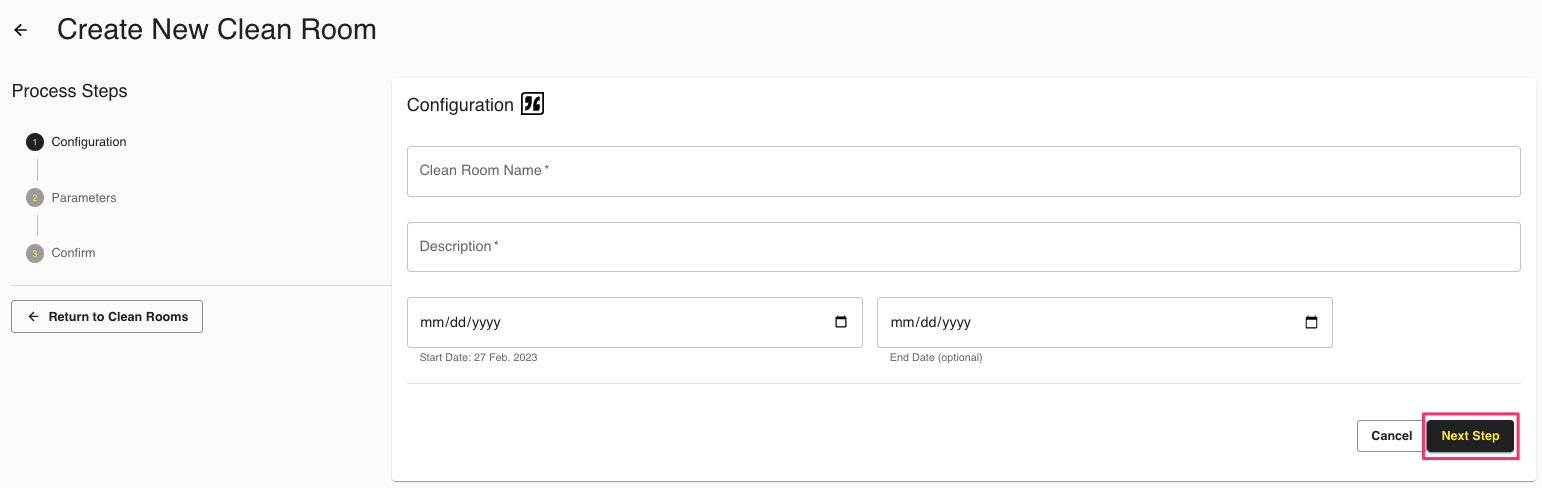
In Configuration , enter the following: a name for the clean room, a description, and start and end dates (optional).
Clean Room Name: Enter a unique name for the clean room
Description: Enter the description of the clean room.
: and End Date: Enter the start and end dates for the clean room. The end date is optional.
Region: Select the region for the clean room from the list.
Note
If an end date is configured, when the clean room reaches its end date, it becomes a "Read Only" clean room. No new question runs or datasets can be configured and new partners cannot be added. To reactivate an expired clean room, update its end date to a new date in the future.
Click .
On Data Control Parameters, specify the following additional layers of privacy protection to your query outputs, which are typically based on the privacy tolerance of your organization (to learn more, see "Privacy-Preserving Techniques and Clean Room Results"):
Data Decibel: Configure the level of noise to prevent identifying an individual or consumer. Noise is configured at a clean room level and applied to specific measures that will be determined during the question creation process.
Crowd Size: Configure the k-minimum value or the threshold that must be achieved by a specific measure in the query for it to display results. If the number of users is less than this value, the row of data in the query result is redacted.
Click .
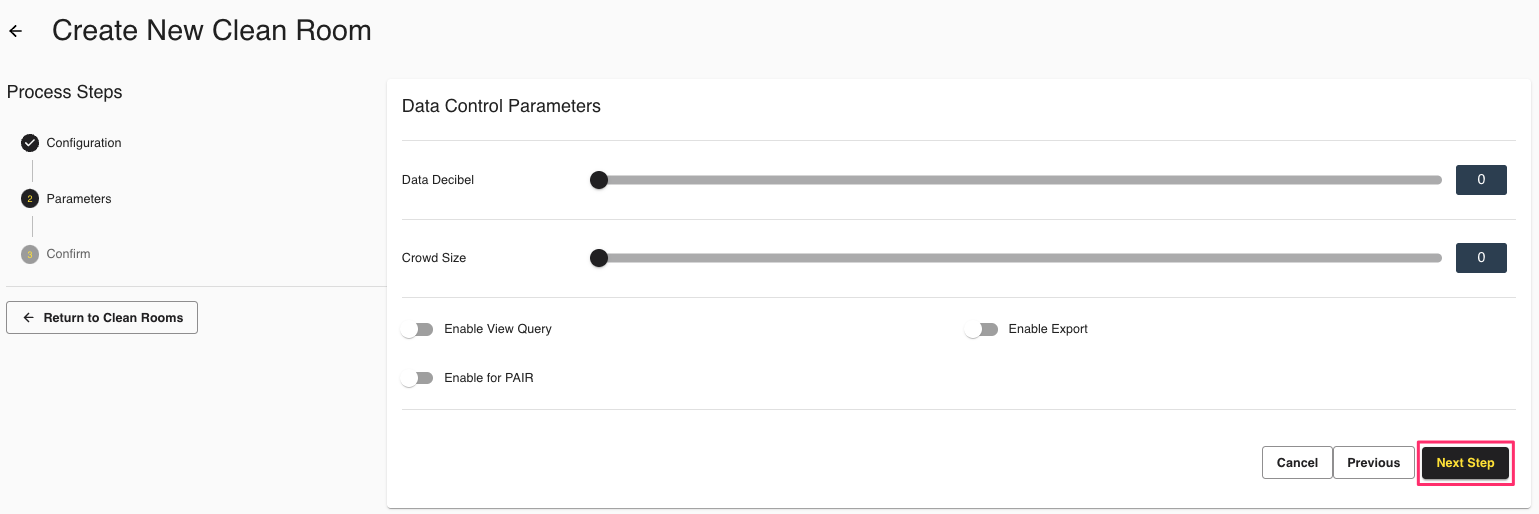
Confirm your clean room configuration settings and click .
Next to the newly provisioned clean room, click Edit.
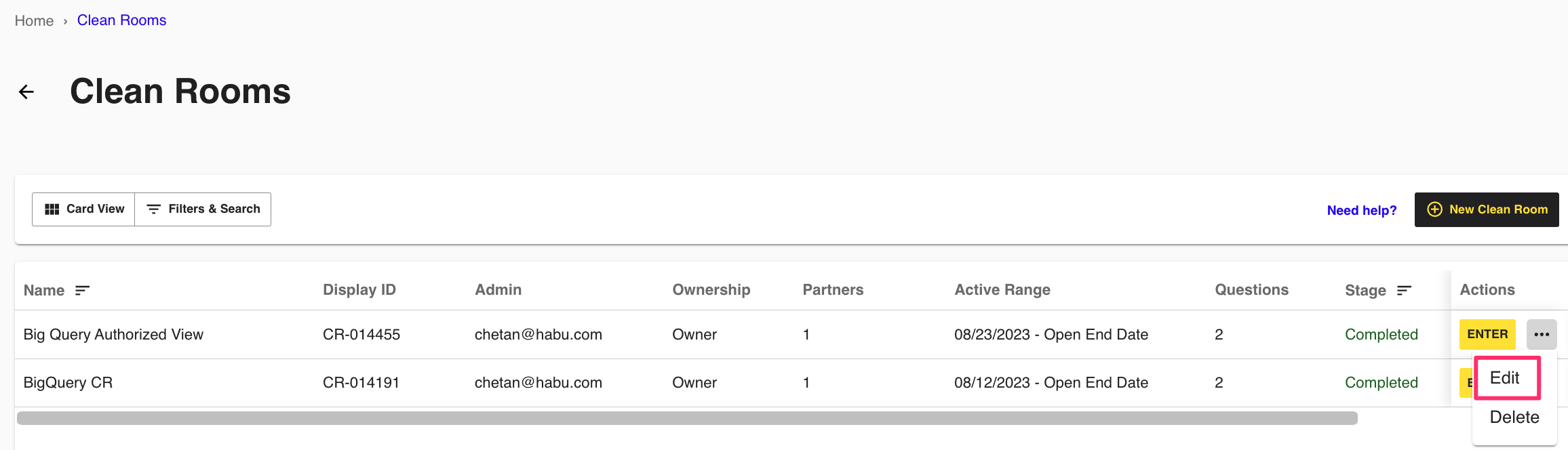
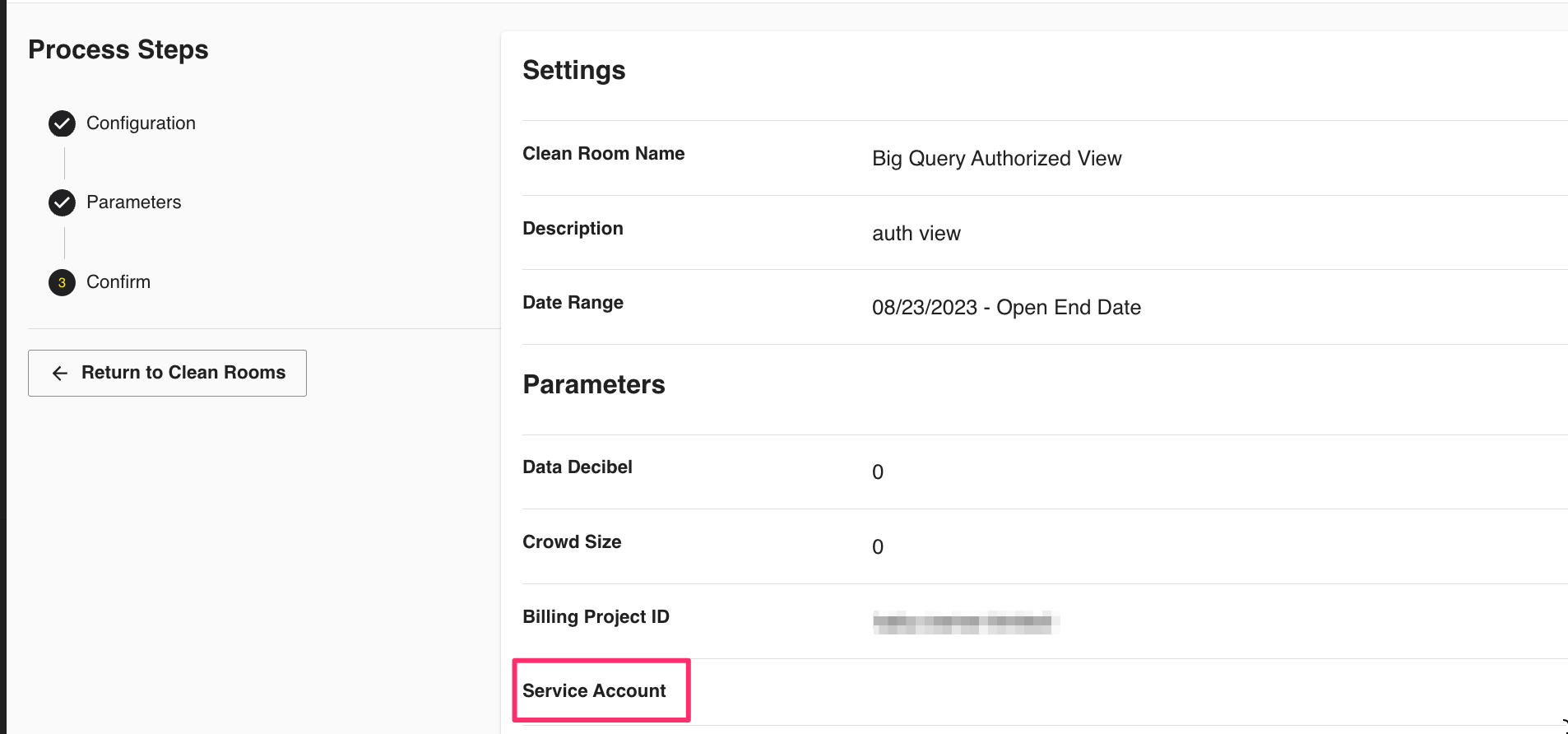
Skip to the third and final step titled Settings. The service account will appear next to the Service Account line item.
Apply the service account roles, created in the "Create Authorized Views" section above, to the service account.
Now that you've set up the required permissions and linked your Google Service Account credentials, you are ready to configure a data connection.