Encrypting Files for Uploading
Files containing PII (personally identifiable information) (or any files containing information that you consider to be confidential) should be encrypted before transferring to LiveRamp. GPG/PGP-encrypted files using LiveRamp’s public key can be automatically decrypted when automated ingestion is set up.
Caution
LiveRamp's public key for encrypting files was updated on May 8, 2025. To download the new public key, click here or see the "Download the Current Encryption Key" section below.
You can continue to use the previous key (which was updated on March 7, 2024) until July 2, 2025. After July 2, 2025, only the new key can be used and If you try to upload a file that was encrypted with a previous encryption key, the file upload will fail.
Be sure to name your file correctly before encrypting it.
Overview of Encryption Keys
A key always has two parts: a public key, which is widely distributed, and a private key, which is secret and remains only with the holder of the key.
PGP also has the notion of master and subkeys. Master keys can be used to create any number of subkeys, which are then tied to that master.
Master keys are considered to represent the overall "identity" of a person/entity; when you encrypt a message to someone for example, you use their master key as the recipient identifier.
Keys can be marked with various capabilities. They can be used to "sign" some piece of data (I can prove cryptographically that a message is from me), "encrypt" data (I encrypt data with a recipient’s public key so that only the corresponding private key can decrypt it), or "certify" another key (I attest that another key really does belong to the person who claims to own it).
In common practice, a person will generate one master key and then subkeys for as many functions as they require.
The subkeys are considered more ephemeral: the user may configure them to expire after some amount of time and then issue new ones, all tied to the same original master key (again, the master is a stable identity for that person).
LiveRamp's Public Key
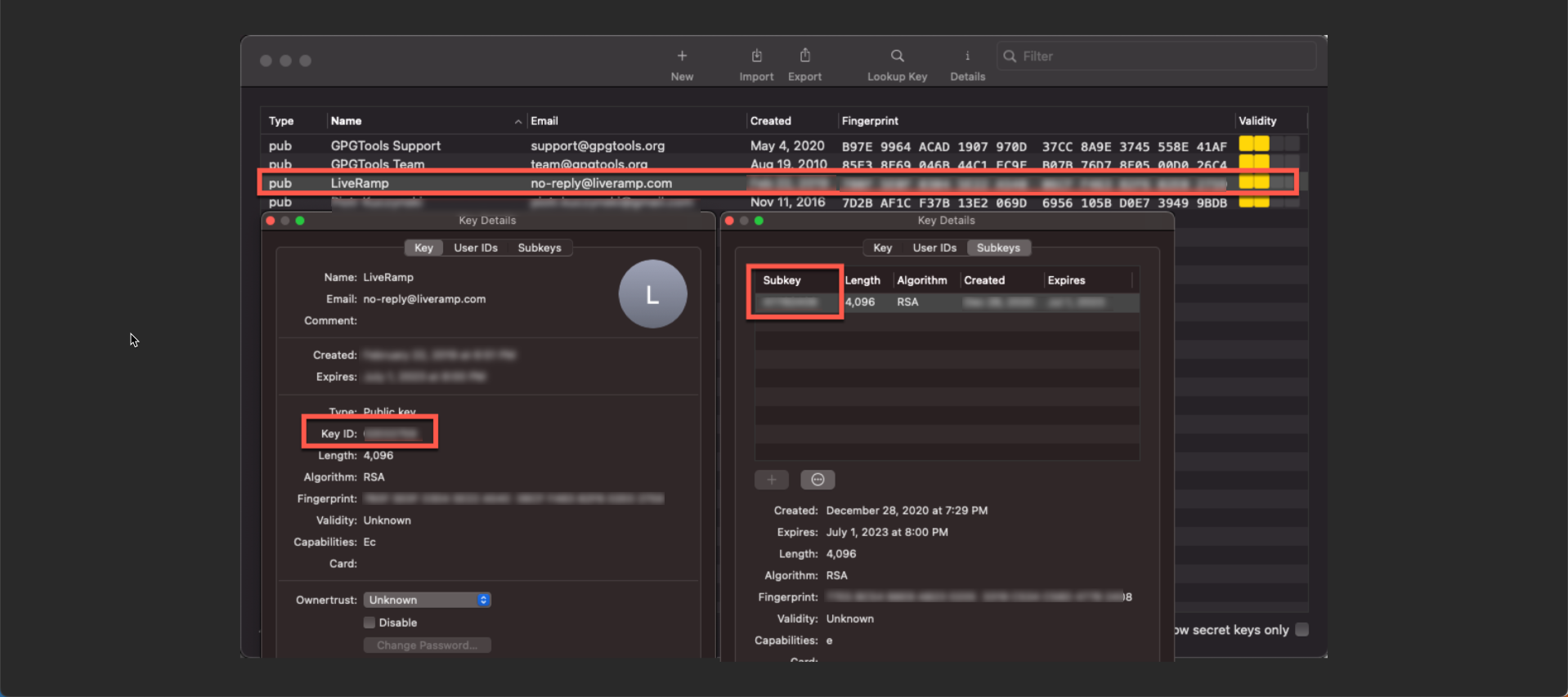
In the public key file we share, there are two keys: a primary key and a subkey. Only the subkey is flagged to be used for encryption. They are both RSA keys, so technically, they could both be used to encrypt. If the software tool that you are using is not respecting usage flags, it might just select the first key with a supported encryption algorithm, and that would probably be the primary key since it shows up first in the file.
Caution
LiveRamp's master key is not authorized for encryption. Files encrypted using the master key cannot be decrypted by LiveRamp and are not able to be imported. The GPG software enforces this restriction, but we can't guarantee that any third party or custom software will do so.
See below for a screenshot of a GPG keychain with the key file imported and showing the KeyID for the overall key is the master key, but it also contains a subkey:
Download the Current Encryption Key
Click here to download LiveRamp's current public encryption key, which was updated on May 8, 2025.
Note
Once you've downloaded the file, if your computer asks you to choose an application to open the file, select a text editor.
You can continue to use the previous key (which was updated on March 7, 2024) until July 2, 2025. After July 2, 2025, only the new key can be used, and if you try to upload a file that was encrypted with a previous encryption key, the file upload will fail.
Keep the following in mind when updating your encryption key:
As of August 2, 2021, LiveRamp no longer accepts files that were encrypted using the master key rather than the encryption subkey.
The master key will continue to exist and appear on your GPG keychain because it is the source of the encryption subkey, but the encryption subkey is what is needed for successful encryption.
Caution
While GPG software restricts the use of the master key for encryption purposes, we cannot guarantee that any third party or custom software will do so.
Validate the Current Key
Once you've updated the key, you can validate that you're using the new encryption key by running the following command on an encrypted file from your gpg software: gpg --list-packets [filename]
If the correct encryption key was used, you will see ID 26598156F2C8792D in the response.
Compressing and Encrypting a File
To both compress and encrypt a file, use one of the two methods listed below:
Use the built-in compression functionality of gpg.
Compress the file, and then encrypt it. This will produce a .gz.gpg file extension, for example.
Encrypt a File Via the Command Line
You can also encrypt files using the command line. To do so, enter the following commands into the command line:
$ gpg --import liveramp_2025.pub.asc $ gpg --encrypt-files -r no-reply@liveramp.com files_to_encrypt
Note
After entering the above commands, you might get a message saying: "There is no assurance this key belongs to the named user." You can safely ignore this warning. When the command line prompts whether you would like to use the key anyway, enter "y" to generate the encrypted file.