LiveRamp Identity in the ADX Marketplace
LiveRamp's Identity in the ADX Marketplace allows you to access the following solutions:
RampID Identity Resolution: Resolve online identifiers (cookies, mobile device IDs, and CTV IDs) and offline identifiers (personally-identifiable information, such as names, addresses, phones, and emails) to RampIDs, LiveRamp’s persistent pseudonymous identifier for persons and households. Identity resolution allows you to have a more holistic view of your data at an individual or household level. A common use case for identity resolution includes resolution of device-based exposure logs from DSPs into RampIDs, driving more accurate insights and analytics. You can also input an individual-based RampID and get back any household-based RampID that might be associated with that individual. For more information, see "Perform RampID Identity Resolution Through ADX".
Known Identity Resolution: Resolve your consumer PII into LiveRamp Known IDs, which allows you to consolidate your consumer PII across fragmented data sources into a unified view to gain an accurate customer profile, improving customer data management and powering effective customer engagement. For more information, see "Perform Known Identity Resolution Through ADX".
Identity Translation: Each LiveRamp identifier is encoded uniquely for each LiveRamp client. This solution allows you to translate partner-encoded identifiers (like Known IDs or RampIDs) in one domain to Known IDs or RampIDs in another domain so that they can be used by another party. For more information, see the following articles:
You can access LiveRamp Identity within the AWS ADX Marketplace, meaning identity resolution and translation can be performed within AWS.
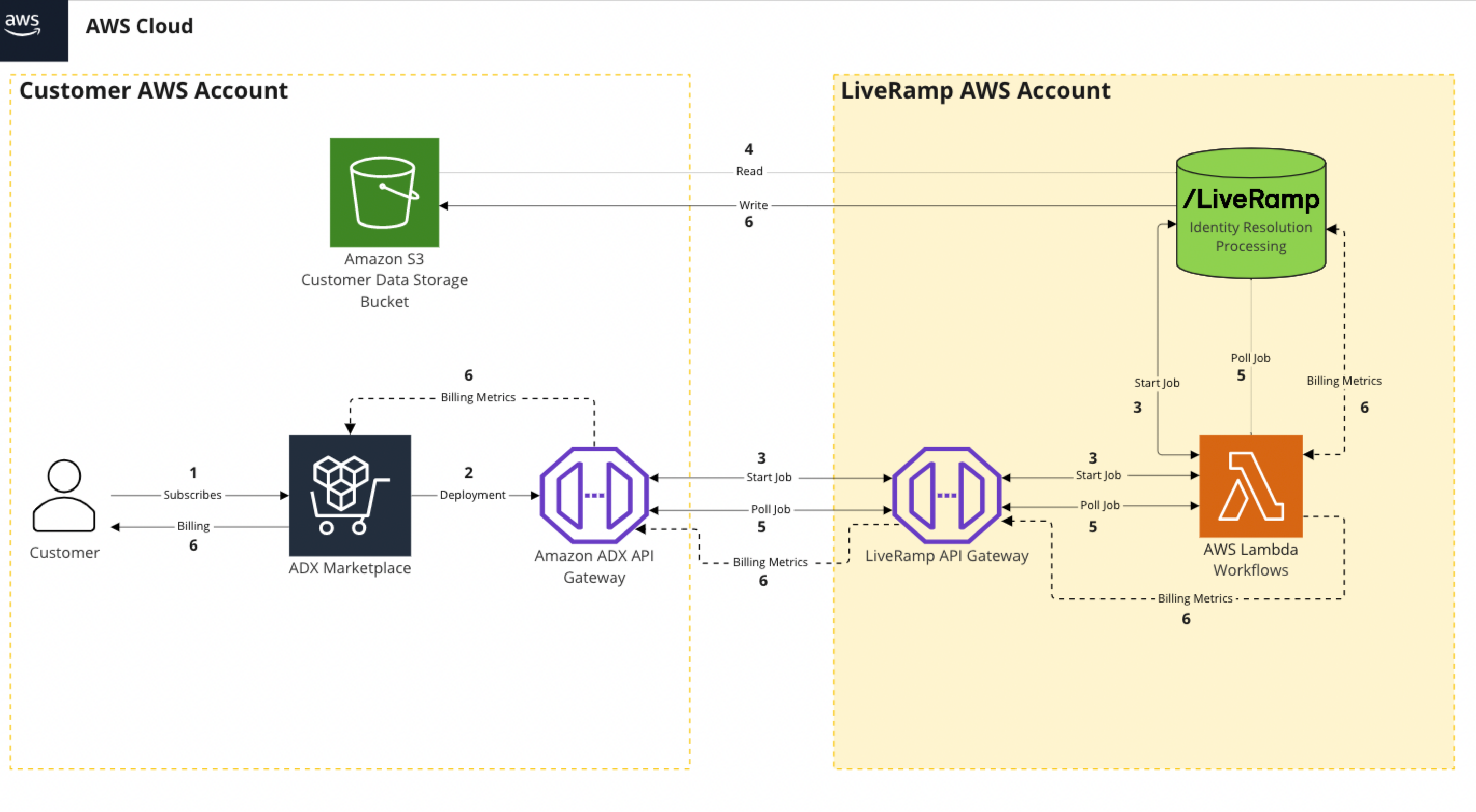
Workflow Diagram
See the diagram below for a representation of the identity workflow in AWS.
Enable LiveRamp Identity in ADX
Before you can perform identity resolution or translation in ADX, the following steps must be completed:
Note
To contract with LiveRamp directly (outside of the ADX Marketplace), contact your LiveRamp representative.
You subscribe to LiveRamp Identity Resolution via the ADX Marketplace.
You execute a contract with LiveRamp via the ADX Marketplace listing, which includes the granting of the needed authorization and credentials.
You perform RampID Attestation to attest that you will follow appropriate usage of RampIDs, and/or the LiveRamp Data Ethics team performs a review.
You provide LiveRamp with your AWS cloud region (for example, “US-East-1”) prior to the contract execution.
Note
The ADX offer will be made and accepted in US-East-2, and API calls will be made from US-East-2.
The region you provide for your contract is where your buckets need to be. As long as your buckets are in US-East-1, your job (compute at LiveRamp's end for your job) will run in US-East-1 and will not incur cross-region data transfer costs. For bucket regions other than US-East-1 and US-West-2, you need
cross regionto be true in your incoming request, and it will run in US-East-1.
You provide LiveRamp with access to your AWS S3 buckets (see the section below for more information).
Once these steps have been performed, see the appropriate article below for information on performing the desired process:
Provide Access to LiveRamp
Data files for processing must reside in an S3 bucket to be picked up by the Identity service. LiveRamp must be given IAM User access to the S3 bucket via the bucket policy provided below.
The process uses two S3 bucket locations, one for input files and one for output files. LiveRamp recommends that the S3 buckets utilized should be used exclusively for LiveRamp processing and host no other data outside of the files necessary for processing. Enabling AWS' default server side encryption policy, SSE-S3, is recommended for both locations (for more information, see this AWS article).
Note
While you can use one set of S3 buckets for more than one LiveRamp identity process (for example, if you'll be performing both identity resolution and translation), you might prefer to have different sets for each process type.
We also recommend that access granted to LiveRamp follow the principles of least privilege, meaning that you provide LiveRamp the minimal access required to process your data.
Input Bucket Permissions
The S3 permissions needed for the input bucket for LiveRamp processing are:
{
"Version": "2012-10-17",
"Statement":
[
{
"Sid": "LiveRampInputS3Acl",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::715724997226:user/adx-customer-s3-user-prod"
},
"Action": [
"s3:GetObject",
"s3:GetBucketAcl",
"s3:ListBucket",
"s3:GetBucketLocation",
"s3:GetObjectVersion"
],
"Resource": [
"arn:aws:s3:::<input-bucket-name>",
"arn:aws:s3:::<input-bucket-name>/*"
]
}
]
}Output Bucket Permissions
The S3 permissions needed for the output bucket for LiveRamp processing are:
{
"Version": "2012-10-17",
"Statement":
[
{
"Sid": "LiveRampOutputS3Acl",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::715724997226:user/adx-customer-s3-user-prod"
},
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:GetBucketAcl",
"s3:DeleteObjectVersion",
"s3:ListBucket",
"s3:DeleteObject",
"s3:GetBucketLocation",
"s3:GetObjectVersion"
],
"Resource": [
"arn:aws:s3:::<output-bucket-name>",
"arn:aws:s3:::<output-bucket-name>/*"
]
}
]
}
Use KMS Encryption
If you plan to use key management service (KMS) encryption on the input and output buckets, update your policy to allow our IAM user access to the key. Configuration can be completed through the following:
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::574365156811:role/Admin",
"arn:aws:iam::715724997226:root"
]
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
}