LiveRamp Data Security Overview
When you send your data to LiveRamp, we protect your data at every step of the process to ensure that confidential information is never compromised.
Your consumer data (PII and CRM data) is sent to the LiveRamp SFTP server.
To reach our SFTP server, the data goes through a firewall. To ensure your data are fully protected while it’s on the SFTP server, we recommend that you use our public PGP key to encrypt your data before sending it.
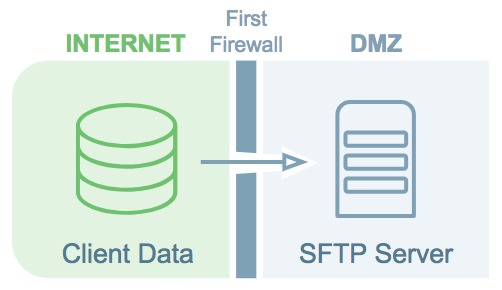
Your data travels from the SFTP server to the LiveRamp processing environment.
Your data are mirrored from the SFTP server into our LiveRamp processing environment; this copy exits the DMZ through a second firewall. The data on the SFTP server is securely deleted to NIST standards within 48 hours.
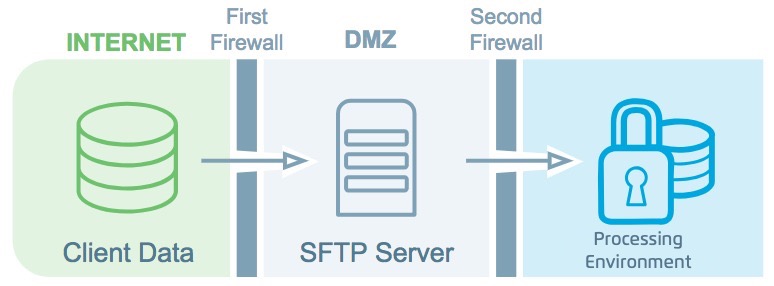
Your data are pseudonymized, matched, and activated.
Your files are decrypted and all PII (personally identifiable information) is irreversibly obfuscated by a series of salting and hashing. This obfuscated data is matched to the obfuscated data in our offline identity graph to link each record to a RampID, our pseudonymous universal identifier.
Through our online identity graph (powered by our Match networks), we translate these RampIDs into partner-specific cookies, mobile device IDs, and other online IDs so they can be distributed to the destination platform of your choice.
The original PII files are maintained encrypted in storage for 30 days from the time of upload in case there are issues during processing (7 days for EU data files). All data are then securely deleted to NIST standards (certificates of deletion can be provided upon request).
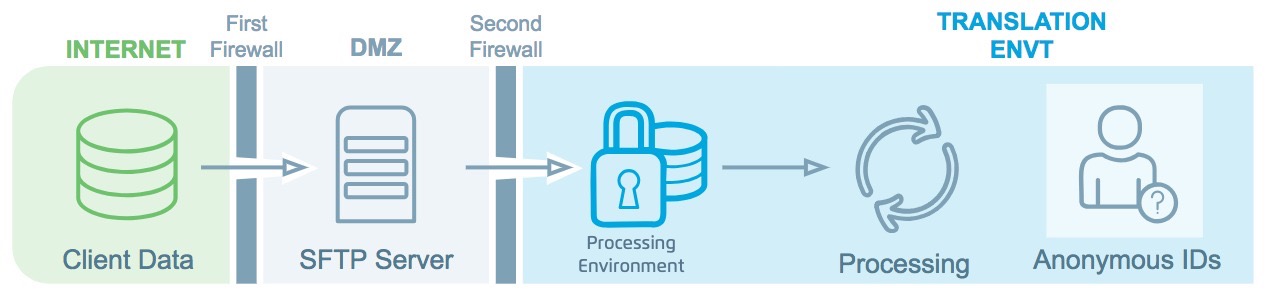
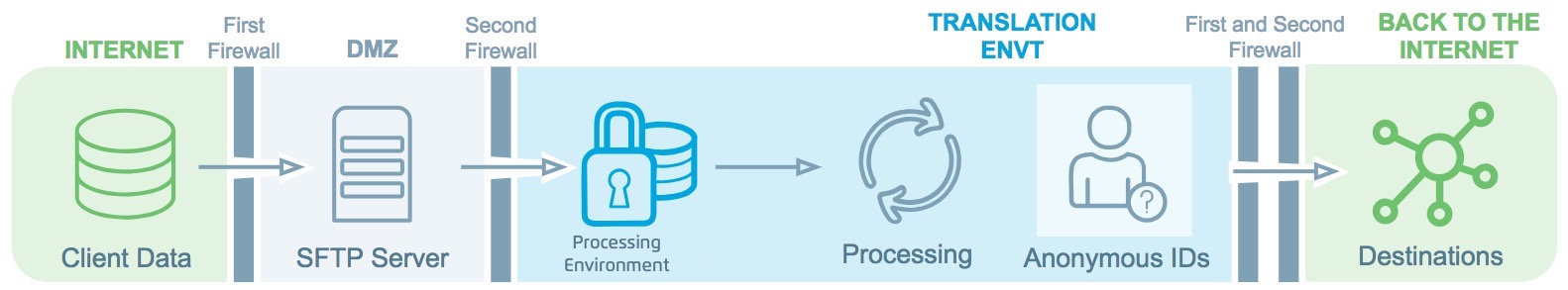
The pseudonymous IDs are distributed to your chosen destinations.
Your pseudonymized data are sent to your chosen destinations (our client partners) via SFTP, S3, GCS, or API.
Definitions
DMZ: In computer security, a DMZ (or demilitarized zone) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted network, usually a larger network such as the Internet.
Firewall: In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted internal network and untrusted external network, such as the Internet, so that your data are protected from hacks and breaches.
FAQs
What is the LiveRamp Translation Zone process/flow?
The Translation Zone process is an essential component of all of our identity-related services. Data (PII + CRM data) is sent to LiveRamp via SFTP, which resides in an external-facing DMZ. The data are then mirrored into the LiveRamp processing environment through another firewall. Once received, the data sits behind our firewall, encrypted at rest, for a limited period (30 days for U.S. data and 7 days for EU data). Within the translation zone, PII is decrypted (loaded into memory) briefly in order to be replaced with a 16-character Abilitec link, which is then salted and hashed twice, converting it to a RampID (our pseudonymous identifier).
What security measures protect LiveRamp's Translation Zone?
The translation zone is built on a defense-in-depth security infrastructure catered to the LiveRamp processing environment. It includes a tiered firewall structure, segmented network zones, translation environment, intrusion detection capability, event monitoring/analysis, and access controls.
Does LiveRamp adhere to any information security frameworks for management/policy? Does LiveRamp maintain any security certifications?
Yes; the LiveRamp Security Policy is based on industry-leading frameworks such as NIST 800-53 and ISO 27001. LiveRamp is pursuing ISO 27001 certification and has a SOC 2 Type II report, which can be sent for your review upon request.
What is LiveRamp’s data access control process?
LiveRamp adheres to role-based access, and the Principle of Least Privilege (PLP), which means that privileged access to client data (or confidential data) or our system is granted only to personnel whose role requires this access, or for some other demonstrable business need.
Does LiveRamp encrypt client data at rest?
Yes; encrypted client data that is uploaded to LiveRamp remains encrypted at rest (i.e., in storage). Clients can send encrypted data to LiveRamp using the LiveRamp 4096-bit public PGP key (for more information, see "Encrypting Files for Uploading").
Who should I contact for further questions?
Contact your account representative, who will connect you with the appropriate LiveRamp contact to answer your questions.